Months ago I wanted to try a Fortigate at home to learn from it by using Fortios, in the past I had to deal with 100D's on our network. I bought a cheap Fortinet Fortigate 90D for 50€ witch is fast, but could be troublesome as stated by some specialists. For most home situations it wil be fast enough with up to 1G connections. Basically one has a statefull packet inspection (SPF) firewall what means that traffic is checked on rules for TCP/IP connections and traffic shall be blocked or denied if not.
Behind this firewall there is a Netgear RBR23 Mesh wifi network in AP mode. The advantage of this configuration is a smoother internet experience. The Wifi part only has to take care on transport, while routing and firewalling is being provided by the Fortigate firewall.
Connecting to the 90D and default setup of interfaces:
After a factory reset the Fortigate starts up in a default configuration with only internal communications possible. Thru DHCP your computer wil get an IP addres and network settings to communicate with the firewall. The firewall can be reached on https://192.168.1.99. One can ignore the warning due to a improper certificate.
The default Username is admin, one shall be asked to configure a Password, or one can do that later on. After this go to Network in te menu, select Interfaces.
Dubbel tap on Internal and configure the internal interface as stated below, the end IP addres of the internal range is extended up to 192.168.1.250, the addresses below 192.168.1.99 can be used for fixed IP servers or systems like your NAS if you have one. The role of the interface is LAN, and I have set "DNS Server" to "Same as interface IP". Below these settings I personally enabled Device Detection, Active scanning and STP as a personal preference.
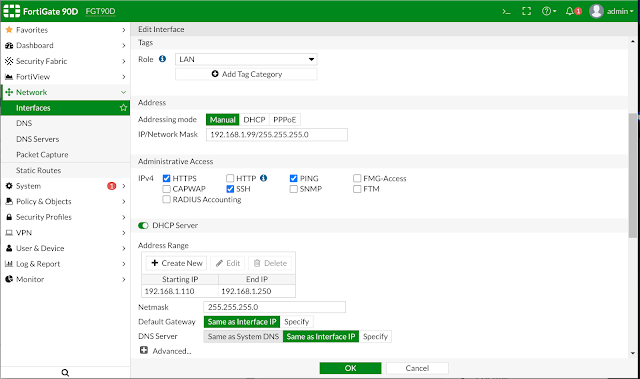
I have disable all administrative acces on the WAN1 interface. Click on OK to save the configuration. If one wants to, open the WAN2 interface and disable it if it is not used.
Again go to the network menu and select Static Routes and in the page select Create New. You can leave the default route a-is. On interface select your WAN interface ans leave the other options as-is and click on okay.
If we get back to the menu, go to Policy and Objects there wil be a default rule that allows all traffic. In the picture below you see the rules I use on the fortigate at home. By now if the internal and external world is connected to the interface Internet could be up and running.
Latest firmware!
The latest firmware is 6.0.18 that can be found on the internet on a thorough search. If one wants to use VPN for remote control the latest version is a necessity for the lower versions are unsafe, in my experience this version is somehow faster then the previous one.
No License mode
I do not have a license for the NGFW features, but they can be used for interest or investigations. These features, if enabled in System > Feature Visibility, can give information on internet usage, but cannot be used any further specifically for it shall block traffic due to a missing license.
The WEB Filter can be used and provides information in logging and Fortiview but all categories should be set to monitoring. The WEB filter has impact on your download speed that shall be played down because certificate inspection is required.
Application control can be used the same way with all categories in Monitoring mode, without impact on internet speed and can provide useful information in logging and Fortiview.
SSL inspection impacts speed traffic deeply so I created a no-inspection rule as can be seen here, the Inspection mode is default in a firewall rule.
DNS Security
There is a way DNS security can be used on the Fortigate and keep enemies out of your network. First one has to enable DNS Database in System > Feature visibility, than in Network DNS specify your preferred DNS server (ours are Next-DNS) and click on Apply.
After that in Network > DNS servers, select create new and configure an internal DNS server on the Internal Interface and select Forward to System DNS and click on OK, you now have an internal system that keeps up DNS entries to serve your internal network. After this one has to setup Fabric Connectors in Security Fabric as can be seen in the picture below. In the section Thread feeds you can configure IP Addres feeds. After some investigations I came on the following IP databases that provide up to 600 million addresses that are unsafe or are known to obscurities. More on these lists can be found here at Firehol. Take a close look on update times for the lists, these times can be configured in each IP thread feed, this defaults to 5 minutes which is way to short and impact firewall performance when using more lists.
After configuring the IP thread feeds you have to add them to the DNS Filter in Security Profiles, and add this profile toe your default Policy as stated below in this picture and enable Allow en Log DNS requests.DNS in the default policy that I have called default allow. IPS
IPS can be used, but remember the rules are old. I rarely see something coming by in the logs. To protect internal systems it is configured as can be seen below the settings can be found in Security Profiles > IPS. The rate Based Signatures are enabled to see if something is happening on the outside WAN interface.
Speed and System Improvement
Some things can be done to make the Fortigate running a little faster. In System > Feature Visibility, disable the things that are not used. Be careful on this, some things should be kept on.
Another improvement is lowering timeouts on connections so the number of connections is 25-50% lower what frees memory and CPU for handdeling these connections. You need to do this in the command interface (CLI) that can be opened in the web interface or over ssh to your firewall. The settings that can be adjusted are:
config system global
set tcp-halfclose-timer 30 [ default 120 s ]
set tcp-halfopen-timer 30 [ default 60 s ]
set tcp-timewait-timer 0 [ default 120 s ]
set udp-idle-timer 60 [ default 120 s ]
end
Source: Fortinet Community
Extended Interface Security Settings
Security can be improved on the Interfaces. On the WAN (outside interface), Ident is disabled (set port 113 to stealth) and Proxy IP ARP is disabled on all interfaces. This advice came along investigating the firewall with Firewall Analyzer from ManageEngine that can be used dree for 30 days. Disabeling Proxy IP ARP had no impact on internal communications. These modificationd can be made in the cli:
config system interface
edit wan1
set arpforward disable
set ident-accept enable
next
edit wan2
set arpforward disable
next
edit modem
set arpforward disable
next
edit ssl.root
set arpforward disable
next
edit internal
set arpforward disable
next
end
SSL/TLS on this FG90D
This firewall is limited to TLS version 1.2 while a lot of traffic these days is at version 1.3. This is a limitation for SSL inspection. If one wants to overcome this look voor a cheap 30E or 50E that are at FortiOS 6.2 where this device is at level 6.0. Version 6.2 has some improvements. For example the Fabric IP connectors are presented as an addres object that can be configured in a firewall rule so all traffic to these addresses shall be denied allesys and not in DNS calls only.
FortiExplorer
FortiExplorer is a phone app to manage your Firewall or get some information on it. The free version is very limited.
In this screenshot some of the basic information is shown. In other sections the configuration can be downloaded or uploaded to the firewall to restore an older version. In the limited edition it is possible to edit some settings and disable the SSL VPN interface.
On a phone with the Forticlient with SSL-VPN configured, FortiExplorer can be used from outside on the internet connecting tot the device at home.
Documentation
Lots of documentation is freely available at Fortinet or can be downloaded for this and other firewalls. For the 90D use the FortiOS 6.0 Documentation.
Video's on starting with Fortigate
Critical Note !!!
As of februari 2024 it is advised not to use ssl-vpn anymore due to a flaw in the sslvpnd that is vulnerable to a remote code exploitation. IPsec-vpn is still a valid option and if the device is registered under you own account, Forticloud is a very neet option to control your device safe and remotely with ZTNA.
As of march 2024 a firmware update (6.0.18) became availeble that patched the CVE-2024-21762 that was related to this SSL-VPN problem, but new flwas became available. The new firmware is an improvement to the 90D and gives me better speeds in testing. TLS-1.2 became the default.


















Reacties
Een reactie posten